12 Aug Identity Governance: Liars and Outliers
To provide business agility an organization’s Identity Governance program should constantly manage user access change requests, while ensuring compliance and manage access risks. In order to manage access risk, it is important to identify, quantify, flag and take actions through the Identity Governance process.
Two of the critical Identity Governance access risks involve: Access Liars and Access Outliers.
Access Liars:
Access Liars are access entitlements that are deceiving or inaccurate. These include:
- Out of band access assignments: Access that is granted outside of IGA system without an audit trail of access request or approval. Examples include out of band access not reflected in a timely manner or flagged (actionable) in IGA system.
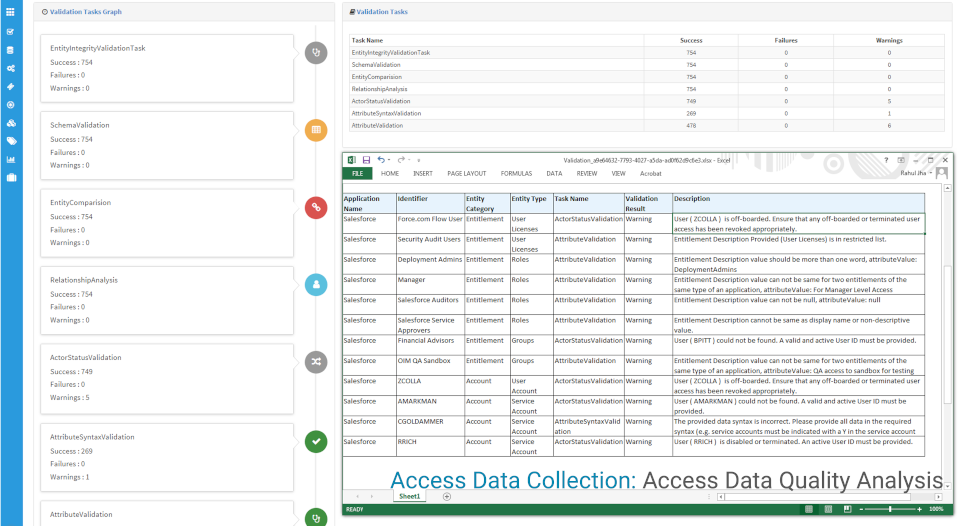
- Access (Entitlements) with missing descriptive information and metadata (risk level): Cryptic IT specific entitlements names increases access risk while being requested or approved by business users.
- Simplified representation of complex entitlements with permission (privileged access) attributes: like groups in SAP, RACF, Tandem, Unix etc. A seemingly common entitlement (groups like “staff”, “wasApp”) gets assigned elevated permissions (write access to system/security files, sudo right etc.) and the elevated permissions are not visible/reflected to the IGA platform, it poses security risk that could go undetected.
- Poor Access Data Quality: An access entitlement assigned to a user account with missing entitlement definition, other examples include orphan accounts and entitlements.
Access Outliers:
Access Outliers are excessive, inappropriate and non-confirming access entitlements. These include
- Excessive and inappropriate level of access beyond job function: These are access that are accumulated over time and events:
- transfer, role changes and still retaining earlier access
- access granted for production incident, production deployment and still retained
- Access that violates Segregation of duties (SoD) policies and are not identified /flagged: Toxic combination of access entitlements that violates Segregation of duties (SoD) policies. Other examples include accounts not following standards / policies.
- Orphan Accounts and System Accounts: Orphan account with privileged access and System accounts without an owner.
Addressing Access Liars and Outliers requires organizations to move towards a Continuous Access Compliance model with focus on access risk and context based governance.
Confluxsys Identity Analytics Platform (IAP) incorporates analytics & data quality & context checks to the IGA process to address risk at each stage of Identity Management. Identity Analytics along with Data Quality Analysis, Entitlements Management and Continuous Access Certification (periodic and event driven) ensures compliance and manages access risks.